You’re already acquainted with the myriad advantages of mobile learning, but have you considered data security? Recent statistics highlight some worrying facts in the rapidly evolving landscape of India’s e-learning surge.
- In Q3 2023, India ranked as the 10th most breached country globally, with 369,000 leaked accounts.
- It continues to hold its position as one of the most breached countries worldwide for the third consecutive quarter in 2023, even though there is a decrease in the number of leaked accounts.
- Additionally, India secures the third position in Asia for the number of leaked accounts during the third quarter.
This underscores the pressing need for robust security measures. Despite this, the Indian mobile learning market, estimated at USD 76.08 billion in 2024, is projected to reach USD 230.12 billion by 2029, with a CAGR of 24.78%.
Factors driving growth include the rapid adoption of electronic devices in corporate education, increased IT investment, and the rise of the BYOD (Bring Your Own Device) culture. Advancements in digital learning, enhanced access, and interactive experiences contribute to improved learning.
A recent HP India report highlights the effectiveness of digital learning, with 63% seeing it as fueling creative thinking. Corporate and higher educational institutions globally are integrating smart technology, with digital learning leading to increased learner engagement and accelerated learning. The BYOD trend continues to reshape the employee learning landscape.
As the educational paradigm shifts, understanding the significance of data security becomes paramount. In a country where mobile education is redefining traditional learning methods, this article will unravel 10 winning strategies to fortify your firm’s mobile learning endeavors. Stay tuned to seamlessly integrate education and security, safeguarding your transformative journey effectively.
Table of Contents
Maximize the Advantages of Mobile Learning: 10 Killer Tips to Ensure Data Security

1. User Authentication and Access Control
You wouldn’t want unauthorized access to your personal information, right? Well, the same goes for the data in your mobile learning systems.
Implementing robust user authentication ensures that only authorized individuals can access sensitive educational data. In fact, research from Cybersecurity Ventures emphasizes the significance of this strategy, stating that 81% of data breaches involve weak or stolen passwords.
By incorporating strong authentication measures, you significantly fortify your defense against potential security threats. So, let’s explore how proper user authentication and access control form the foundation of a secure mobile learning environment:
Measures: User Authentication:
- Require Strong Passwords: Ensure users create passwords with a mix of letters, numbers, and symbols.
- Implement Multi-Factor Authentication (MFA): Add an extra layer of security by combining passwords with verification codes sent to the user’s mobile device.
Measures: Access Control:
- Role-Based Access Control (RBAC): Assign specific roles to users, granting access based on their responsibilities.
- Regularly Review and Update Access Levels: Periodically assess and adjust access privileges as roles and responsibilities evolve.
Ad: PlayAblo’s Enterprise-Grade Micro-Learning platform is built for millennial learners. Micro-Learning, assessments, and gamification features ensure learning outcome measurement and sustained engagement.
Find out more and request a custom demo!
2. Secure Data Encryption
When it comes to safeguarding sensitive information in your mobile learning environment, secure data encryption plays a pivotal role. This strategy ensures that your data remains confidential, whether it’s in transit or at rest. Let’s explore the measures to fortify data encryption:
Measures: Secure Data Encryption
- Use Advanced Encryption Protocols:
- Employ cutting-edge encryption standards to enhance the security of data during transmission and storage.
- Stay abreast of the latest encryption technologies to continuously strengthen your protective measures.
- Implement End-to-End Encryption:
- Guarantee comprehensive data security by implementing end-to-end encryption, safeguarding information from its source to its final destination.
- This ensures that even if intercepted, the data remains indecipherable to unauthorized entities.
For instance, you can utilize Advanced Encryption Standard (AES) to secure data transmission and storage. AES, recognized as a leading encryption algorithm, employs sophisticated cryptographic techniques to protect information. Now, let’s consider an advancement in encryption technology – Post-Quantum cryptography.
Staying abreast of the latest developments, you become aware of Post-Quantum Cryptography, a cutting-edge encryption approach designed to withstand the potential threats posed by quantum computers. Recognizing its enhanced security features, you swiftly integrate this technology into your mobile learning system.
By embracing it, you ensure that your data remains resilient against evolving cyber threats. This proactive approach not only fortifies the security of your mobile learning environment but also demonstrates a commitment to staying ahead of potential vulnerabilities.
3. Regular Security Audits

Regular security audits are instrumental in maintaining the robustness of your mobile learning environment. These audits serve as proactive measures to assess and enhance the effectiveness of your security protocols. Let’s delve into the significance of regular security audits:
Measures: Regular Security Audits
Companies that conduct regular security audits experience 40% fewer security breaches compared to those that don’t. Regular audits contribute significantly to overall cybersecurity resilience. Here’s how you can achieve the same:
- Conduct Periodic Security Audits:
- Regularly schedule comprehensive security audits to evaluate the effectiveness of your existing security measures.
- These audits involve systematic examinations of security policies, practices, and technologies to identify potential vulnerabilities.
- Address Vulnerabilities Promptly:
- Swiftly address and rectify any vulnerabilities identified during security audits.
- This proactive approach minimizes the window of opportunity for potential security breaches.
4. Employee Training on Security Protocols
Ensuring that your employees are well-versed in security protocols is paramount for maintaining a secure mobile learning environment. Proper corporate training empowers them to recognize and respond to potential threats. Let’s explore how employee training on security protocols can be achieved:
Measures: Employee Training on Security Protocols
- Mandatory Security Training:
- Enforce regular security training sessions for all employees involved in the mobile learning process.
- Cover essential topics such as recognizing phishing attempts, creating strong passwords, and adhering to secure data handling practices.
- Simulate Security Threats:
- Conduct simulated security exercises to provide practical experience in responding to potential threats.
- This hands-on approach enhances employees’ ability to identify and mitigate security risks effectively.
Consider a scenario where employees undergo mandatory security training sessions that include simulated phishing exercises. During these simulations, employees receive emails mimicking common phishing attempts. Those who successfully identify and report these simulated threats demonstrate a heightened awareness of potential risks.
As a result of this training, employees become more adept at recognizing and responding to actual security threats in the mobile learning environment. This proactive approach significantly strengthens the human element in your security strategy.
5. Implementing Multi-Factor Authentication

We have briefly touched upon this strategy but let’s now explain this in more detail.
Did you know that 75% of data breaches are perpetrated by outsiders, with 25% involving internal factors?
To mitigate this risk, implementing Multi-Factor Authentication is a pivotal strategy for fortifying your mobile learning program.
Measures: Implementing Multi-Factor Authentication
- Biometric Authentication:
- Integrate biometric factors such as fingerprints or facial recognition for an additional layer of security.
- Biometric data adds a unique and personalized dimension to the authentication process.
- Adaptive Authentication:
- Implement adaptive MFA that adjusts based on user behavior and risk factors.
- This dynamic approach enhances security by tailoring authentication requirements to specific contexts.
By adopting MFA, you significantly enhance your mobile learning environment’s defense against unauthorized access. This strategic implementation not only aligns with cybersecurity best practices but also addresses the vulnerabilities associated with traditional password-based authentication.
6. Secure Cloud Storage Solutions
The majority of data breaches involve weak passwords. To bolster the security of your mobile learning environment, adopting secure cloud storage solutions is paramount.
Measures: Secure Cloud Storage Solutions
- Choose Reputable Cloud Service Providers:
- Opt for well-established cloud providers with a proven track record of robust security measures.
- Reputable providers invest in cutting-edge technologies to safeguard your stored data.
- Data Encryption in the Cloud:
- Ensure data stored in the cloud is encrypted, adding an extra layer of protection.
- Encryption renders data indecipherable to unauthorized entities even if accessed.
Let’s say your mobile learning platform utilizes a renowned cloud service with robust security features. By employing end-to-end encryption, your stored educational data remains confidential. This ensures that even in the event of unauthorized access, the information remains unintelligible, safeguarding the integrity of your mobile learning assets. The strategic adoption of secure cloud storage solutions not only protects your data but also fosters trust in the learning ecosystem.
7. Mobile Device Management (MDM) Implementation
The BYOD trend is on the rise, with mobile devices becoming integral to the learning process. In fact, 83% of companies have a BYOD policy of some kind. However, 37.9% of employees claim that their employers don’t have policies to secure these phones, laptops, and tablets for work, and 11.1% are unsure.
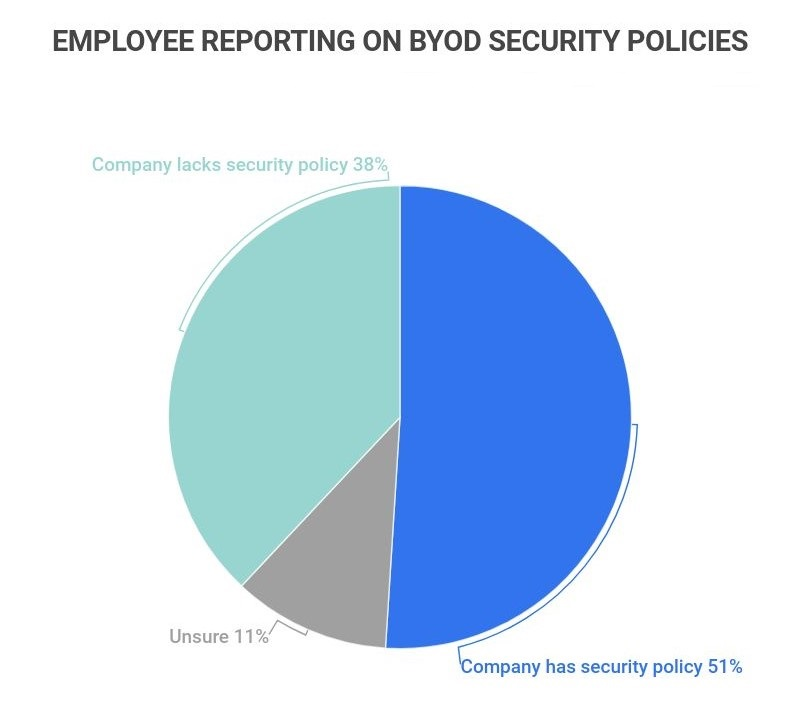
To manage this serious issue, implementing Mobile Device Management (MDM) is crucial. Here’s how:
Measures: Mobile Device Management Implementation
- Enforce Device Policies:
- Implement policies governing the use of mobile devices within the learning environment.
- Clearly define acceptable use, security configurations, and guidelines for device access.
- Remote Wiping Capability:
- Enable the capability to remotely wipe data from lost or compromised devices.
- This feature ensures the protection of sensitive information in case of device loss or theft.
Now, consider a scenario where an employee loses their mobile device containing access to educational materials. With MDM in place, your administrators can remotely wipe the device, preventing unauthorized access to sensitive information. This demonstrates how MDM implementation not only manages device usage but also serves as a proactive measure to protect the integrity of educational data in a mobile learning setting.
8. Continuous Monitoring and Threat Detection
In maintaining the security of your mobile learning environment, Strategy 8 emphasizes continuous monitoring and threat detection. This proactive approach ensures prompt identification and response to potential security risks.
Measures: Continuous Monitoring and Threat Detection
- Real-time Monitoring Systems:
- Implement systems that provide real-time monitoring of activities within the mobile learning environment.
- Real-time monitoring enables swift responses to suspicious or anomalous behavior.
- Utilize Intrusion Detection Systems (IDS):
- Deploy IDS to detect and alert administrators to potential security breaches.
- These systems analyze network or system activities for signs of malicious behavior.
This strategy serves as a vigilant guardian, constantly watching for potential threats and anomalies. By incorporating continuous monitoring and threat detection measures, your mobile learning environment becomes more resilient against evolving security challenges.
9. Data Back-Up Procedures
Ensuring the resilience of your mobile learning environment involves implementing robust data backup procedures.
Measures: Data Back-Up Procedures
- Automate Regular Back-Ups:
- Set up automated systems to regularly back up crucial data, reducing the risk of information loss.
- Automation ensures consistency and minimizes the chance of oversight.
- Store Back-Ups in Secure Locations:
- Safeguard backup data by storing it in secure, off-site locations.
- This precautionary measure protects against potential physical threats to the primary data storage.
Let’s say, in one of your mobile training sessions, a sudden system failure occurs, jeopardizing important educational content. With automated data back-ups in place, administrators can swiftly restore the system to a previous state, minimizing disruptions to the learning process. This exemplifies the importance of data backup procedures in maintaining the continuity and reliability of mobile learning environments.
Ad: PlayAblo’s Enterprise-Grade Micro-Learning platform is built for millennial learners. Micro-Learning, assessments, and gamification features ensure learning outcome measurement and sustained engagement.
Find out more and request a custom demo!
10. Compliance with Data Protection Regulations
In ensuring the integrity and legality of your mobile learning environment, Strategy 10 focuses on compliance with data protection regulations. Adhering to these regulations is vital for safeguarding user privacy and maintaining trust in the learning ecosystem.
Measures: Compliance with Data Protection Regulations
- Understand and Implement Applicable Regulations:
- Thoroughly comprehend the data protection regulations relevant to your region and industry.
- Implement measures to align your mobile learning practices with the stipulated guidelines.
- Data Privacy Training for Staff:
- Provide training to staff members involved in handling sensitive data, ensuring they understand and adhere to data protection principles.
- This empowers staff to make informed decisions regarding data privacy.
By prioritizing compliance with data protection regulations, you not only uphold ethical standards but also mitigate the risk of legal repercussions. This strategy contributes to the responsible and transparent management of user data in your mobile learning environment.
For example, in India, data protection is primarily governed by the Personal Data Protection Bill, 2019 (PDP Bill), which aims to regulate the processing of personal data of individuals. While the bill is yet to become law, it provides a comprehensive framework for the protection and handling of personal data. Here are some key points relevant to data protection regulations in India:
- Personal Data Protection Bill, 2019 (PDP Bill):
- The PDP Bill outlines principles and obligations for the processing of personal data.
- It introduces the concept of data fiduciaries and data processors and establishes the Data Protection Authority of India (DPA) for oversight.
- Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011:
- These rules under the Information Technology Act of 2000, specify guidelines for the collection and protection of sensitive personal data.
- They provide a framework for entities handling sensitive personal information to implement security practices and procedures.
- General Data Protection Regulation (GDPR):
- While not specific to India, the GDPR may be relevant for organizations dealing with the personal data of European Union (EU) citizens.
- Compliance with GDPR principles can enhance overall data protection practices.
- Sector-Specific Regulations:
- Certain sectors in India, such as healthcare and finance, may have additional regulations governing the handling of sensitive data.
- For example, the Health Data Management Policy under the National Digital Health Mission sets guidelines for the protection of health-related data.
To align mobile learning practices with these regulations, your organization needs to stay informed about updates, conduct regular audits, and implement robust data protection measures. It’s essential to adapt practices to evolving regulatory frameworks to ensure compliance and maintain the trust of users in the mobile learning ecosystem.
Are There Any Challenges in Ensuring Data Security During Mobile Learning?

Mobile learning offers unparalleled flexibility, but it brings forth distinct challenges in upholding robust data security. Effectively addressing these challenges is imperative for preserving the confidentiality and integrity of educational data. Let’s delve into key challenges and corresponding solutions associated with data security in the realm of mobile learning:
1. Device Diversity and BYOD Policies:
Challenge: The diverse array of devices and BYOD policies make standardizing security measures challenging.
Solution: Implement device-agnostic security protocols that accommodate various operating systems. Utilize MDM solutions to enforce consistent security policies regardless of device type.
2. Network Vulnerabilities:
Challenge: Learning over various networks, especially public Wi-Fi, exposes data to potential interception.
Solution: Employ robust encryption protocols to secure data transmission. Encourage the use of Virtual Private Networks (VPNs) for an added layer of network security.
3. Lack of User Awareness:
Challenge: Users may lack awareness of best practices for data security on mobile devices.
Solution: Conduct regular awareness programs and training sessions for educators and learners. Emphasize the importance of secure practices, such as using strong passwords and recognizing phishing attempts.
4. Data Storage in Cloud Environments:
Challenge: Cloud storage introduces concerns about the security of off-site data.
Solution: Choose reputable cloud service providers with strong security measures. Implement end-to-end encryption for data stored in the cloud and regularly assess the provider’s security protocols.
5. Regulatory Compliance:
Challenge: Keeping abreast of evolving data protection regulations is a constant challenge.
Solution: Establish a dedicated compliance team to monitor and adapt policies based on regulatory changes. Conduct regular audits to ensure ongoing adherence to compliance requirements.
6. Mobile App Security:
Challenge: Mobile apps used for learning can be vulnerable to unauthorized access or data leaks.
Solution: Implement stringent security measures within mobile applications, including encryption of data in transit and at rest. Regularly update and patch mobile apps to address emerging security threats.
7. Balancing Security and Accessibility:
Challenge: Striking a balance between robust security measures and convenient access to educational resources is challenging.
Solution: Conduct a risk assessment to identify critical security needs. Implement adaptive security measures that prioritize protection without compromising the user experience.
Addressing these challenges through a holistic approach involving technology, education, and adaptability is crucial. By proactively implementing these solutions, organizations can create a secure and conducive mobile learning environment that fosters learning without compromising data security.
Final Words
As you venture into the dynamic landscape of mobile learning, these ten winning strategies stand as guardians of data security. From user authentication to compliance with data protection regulations, each strategy plays a pivotal role in fortifying your learning environment. By embracing these measures, you not only mitigate risks but also pave the way for a future where mobile learning seamlessly integrates accessibility, innovation, and unwavering data security into your educational journey. Stay vigilant, stay secure, and let knowledge thrive on the mobile frontier.
Ad: PlayAblo’s Enterprise-Grade Micro-Learning platform is built for millennial learners. Micro-Learning, assessments, and gamification features ensure learning outcome measurement and sustained engagement.
Find out more and request a custom demo!








Comments are closed, but trackbacks and pingbacks are open.